Ansible - Example playbook to Patchup Selective packages on RHEL 7 / CentOS and Full Security Patchup
Ansible playbook to Patchup Selective Packages on RHEL 7 / CentOS servers
In this playbook we are going to do Security Patchup and Selective Package Updates. Keeping your system up to date and applying all security patches is an essential task for sysadmins and developers. We can use yum module of Ansible to manages yum packages for RHEL/CentOS based Linux distros. This module can use to install, remove, update on the remote servers for package management. This page explains how to run yum update --security or yum update package-name via Ansible.
In this playbook we are doing 5 tasks
- Gather the rpm packages installed using facts module : package_facts
- Importing list of packages need to be Patchup using variable in directory:
directory : vars
file: package.yml
variable name: myvar (it have list of packages)
- Updating list of packages which are installed only.
- Display installed packages result
- Applying Security Updates only --- passing with variables if required to have full Security Patchup.
Step1: Create variables files for package list
Switch to your playbooks directory:
[root@ansible ~]# cd redhat-playbooks/
Create directory for variable, here I am using "vars"
[root@ansible redhat-playbooks]# mkdir vars/
Create variables file, here I am creating as "packages"
[root@ansible redhat-playbooks]# vi vars/packages.yml
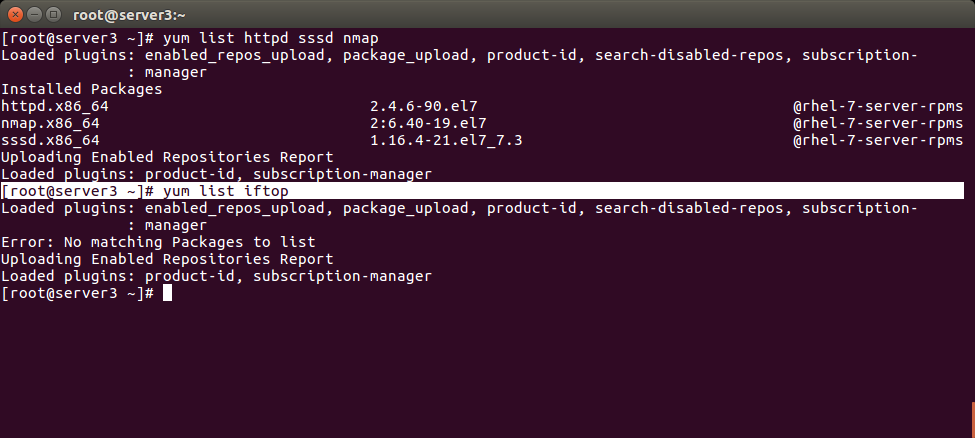
--- myvar: - httpd - nmap - sssd - iftop
Step2: Create Playbook for Selective Package Update
Create Playbook, I am using name "redhat-selective-packages-security.yml"
[root@ansible redhat-playbooks]# vim redhat-selective-packages-security.yml
---
- name: Redhat and Centos Server selective Packages Patchups
hosts: webservers
ignore_errors: yes
force_handlers: yes
tasks:
- name: Gather the rpm package facts
package_facts:
manager: auto
- name: Import variables files
include_vars: vars/packages.yml
- name: Update package
ignore_errors: yes
yum:
name: "{{ item }}"
state: latest
loop: "{{ myvar | default([]) }}"
when: item in ansible_facts.packages
register: install_result
- name: Display installed packages result
debug:
var: install_result
- name: Server is getting FULL SECUIRTY PATCHUP ONLY --- SECURITY
yum:
name: '*'
security: yes
state: latest
when: "'{{ patchup_sec }}' == 'Security'"
tags: ['security']
Step3: Run ansible-playbook without "Security" variable... only for Selective Patchup
[root@ansible redhat-playbooks]# ansible-playbook redhat-selective-packages-security.yml --extra-vars "patchup_sec="
Result for playbook run:
PLAY [Redhat and Centos Server selective Packages Patchups] **********************************************************************************************************************
TASK [Gathering Facts] ***********************************************************************************************************************************************************
ok: [webservers]
TASK [Gather the rpm package facts] **********************************************************************************************************************************************
ok: [webservers]
TASK [Import variables files] ****************************************************************************************************************************************************
ok: [webservers]
TASK [Update package] ************************************************************************************************************************************************************
ok: [webservers] => (item=httpd)
ok: [webservers] => (item=nmap)
ok: [webservers] => (item=sssd)
skipping: [webservers] => (item=iftop)
TASK [Display installed packages result] *****************************************************************************************************************************************
ok: [webservers] => {
"install_result": {
"changed": false,
"msg": "All items completed",
"results": [
{
"ansible_loop_var": "item",
"changed": false,
"changes": {
"installed": [],
"updated": []
},
"failed": false,
"invocation": {
"module_args": {
"allow_downgrade": false,
"autoremove": false,
"bugfix": false,
"conf_file": null,
"disable_excludes": null,
"disable_gpg_check": false,
"disable_plugin": [],
"disablerepo": [],
"download_dir": null,
"download_only": false,
"enable_plugin": [],
"enablerepo": [],
"exclude": [],
"install_repoquery": true,
"install_weak_deps": true,
"installroot": "/",
"list": null,
"lock_timeout": 30,
"name": [
"httpd"
],
"releasever": null,
"security": false,
"skip_broken": false,
"state": "latest",
"update_cache": false,
"update_only": false,
"use_backend": "auto",
"validate_certs": true
}
},
"item": "httpd",
"msg": "",
"rc": 0,
"results": [
"All packages providing httpd are up to date",
""
]
},
{
"ansible_loop_var": "item",
"changed": false,
"changes": {
"installed": [],
"updated": []
},
"failed": false,
"invocation": {
"module_args": {
"allow_downgrade": false,
"autoremove": false,
"bugfix": false,
"conf_file": null,
"disable_excludes": null,
"disable_gpg_check": false,
"disable_plugin": [],
"disablerepo": [],
"download_dir": null,
"download_only": false,
"enable_plugin": [],
"enablerepo": [],
"exclude": [],
"install_repoquery": true,
"install_weak_deps": true,
"installroot": "/",
"list": null,
"lock_timeout": 30,
"name": [
"nmap"
],
"releasever": null,
"security": false,
"skip_broken": false,
"state": "latest",
"update_cache": false,
"update_only": false,
"use_backend": "auto",
"validate_certs": true
}
},
"item": "nmap",
"msg": "",
"rc": 0,
"results": [
"All packages providing nmap are up to date",
""
]
},
{
"ansible_loop_var": "item",
"changed": false,
"changes": {
"installed": [],
"updated": []
},
"failed": false,
"invocation": {
"module_args": {
"allow_downgrade": false,
"autoremove": false,
"bugfix": false,
"conf_file": null,
"disable_excludes": null,
"disable_gpg_check": false,
"disable_plugin": [],
"disablerepo": [],
"download_dir": null,
"download_only": false,
"enable_plugin": [],
"enablerepo": [],
"exclude": [],
"install_repoquery": true,
"install_weak_deps": true,
"installroot": "/",
"list": null,
"lock_timeout": 30,
"name": [
"sssd"
],
"releasever": null,
"security": false,
"skip_broken": false,
"state": "latest",
"update_cache": false,
"update_only": false,
"use_backend": "auto",
"validate_certs": true
}
},
"item": "sssd",
"msg": "",
"rc": 0,
"results": [
"All packages providing sssd are up to date",
""
]
},
{
"ansible_loop_var": "item",
"changed": false,
"item": "iftop",
"skip_reason": "Conditional result was False",
"skipped": true
}
]
}
}
TASK [Server is getting FULL SECUIRTY PATCHUP ONLY --- SECURITY] *****************************************************************************************************************
[WARNING]: conditional statements should not include jinja2 templating delimiters such as {{ }} or {% %}. Found: '{{ patchup_sec }}' == 'Security'
skipping: [webservers]
PLAY RECAP ************************************************************************************************************
If you see in the above results, we get 3 success and one skipping. Coz our server have only httpd, nmap and sssd packages are installed. It skipped for iftop coz package is not installed.
ok: [webservers] => (item=httpd) ok: [webservers] => (item=nmap) ok: [webservers] => (item=sssd) skipping: [webservers] => (item=iftop)
"results": [ "All packages providing nmap are up to date", "results": [ "All packages providing httpd are up to date", "results": [ "All packages providing sssd are up to date",
But we get failed for
"ansible_loop_var": "item",
"changed": false,
"item": "iftop",
"skip_reason": "Conditional result was False",
"skipped": true
}
Below you can check packages installed or not. By yum command on server.
Step4: Apply security patchup run playbook with variable Security
If you want to do Full Security patchup for server you can run below command:
[root@ansible redhat-playbooks]# ansible-playbook redhat-selective-packages-security.yml --extra-vars "patchup_sec=Security"
This will do full security patchup only --- this will not make full update of server. Only Security patchup
Note: This has been tested on RHEL 7 (I didn't tested on CentOS for Security Patchup Only)
Conclusion
The playbook is ready. You can now easily do Security Patchup and Selective Packages Updates from variable file thanks to Ansible.



Hi
hello, your site is amazing.Following your site.